[ad_1]
What is a crisis management plan (CMP)?
A crisis management...
[ad_1]
What is a crisis management plan (CMP)?
A crisis management...
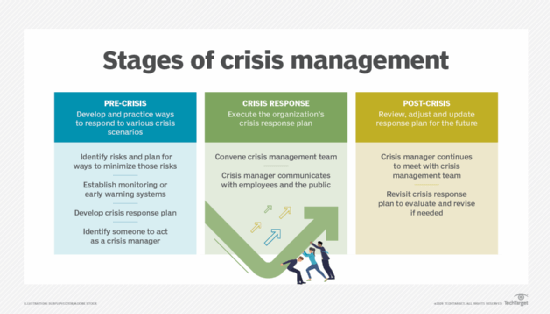
[ad_1]
What is BYOD?
BYOD (bring your own device) is a policy that...
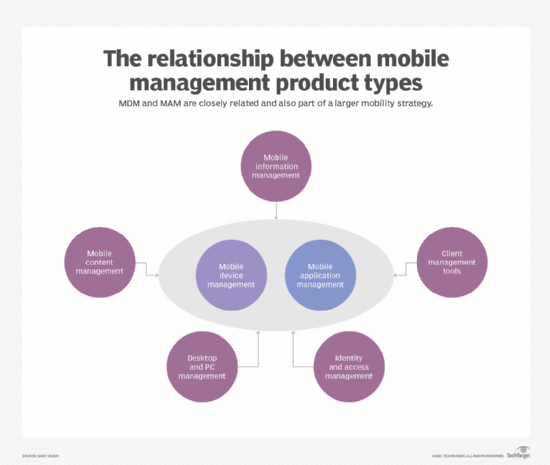
[ad_1]
While AI is taking the world by storm, the gold at the end of...

[ad_1]
It’s a wonderful time to be a Linux user:...
[ad_1]
What is a possession factor?
The possession factor, in a security context, is a category of user authentication credentials based on items...
[ad_1]
What is a privacy impact assessment?
A privacy impact assessment (PIA) is a method for identifying and assessing privacy risks...
[ad_1]
By
Periodic assessments of cybersecurity plans, policies and procedures ensure cybersecurity programs meet...
[ad_1]
Cloud security vendor Wiz discovered 38 TB of private Microsoft data that was accidentally exposed by AI researchers employed by the...
[ad_1]
What is distributed ledger technology (DLT)?
Distributed ledger technology (DLT) is a digital system for recording the transaction of...
[ad_1]
Ransomware is one of the most effective strategies for attacking businesses, critical infrastructure and individuals. This type of malware...
[ad_1]
When a public community college in the state of Washington suffered a ransomware attack, the effects were catastrophic.
“They...
[ad_1]
What is a Common Access Card (CAC)?
A Common Access Card (CAC) is a smart card issued by the Unites States Department of Defense for...